(Update 2014-09-27: corrected Data Protection Act to Computer Misuse Act)
I have been playing around with the world famous shell shock vulnerability, CVE-2014-6271, like many others I am sure. Many have provided some very interesting uses of it, the best one on Twitter was that of instructing the system to update. I would imagine that would still constitute a breach of the Computer Misuse Act since the machine is being altered without the users permission.
I have been playing around with the world famous shell shock vulnerability, CVE-2014-6271, like many others I am sure. Many have provided some very interesting uses of it, the best one on Twitter was that of instructing the system to update. I would imagine that would still constitute a breach of the Computer Misuse Act since the machine is being altered without the users permission.
The reason for this post is to present some interesting
behaviour I noticed when playing around with dash, bash, env and export.
I want to have a way to login to a machine and make sure I
could safely check on things. One of the temporary solutions was to remove bash
and link in dash. dash does not run the loaded script. Once on the machine you
could carry on using dash or attempt loading bash if you feel lucky, if there
is a stored version that is.
I therefore looked to see where the function was loaded and
noticed some interesting behaviour between dash and bash. So on to the test.
Test Case 1:
Test machine, Ubuntu 10.04,
(I have removed .bashrc to limit the amount in the export
list)
We start off by loading up dash, instead of bash.
Fig. 1 – show export via export command, in dash
As seen in fig.1 the clean export list is shown, via the
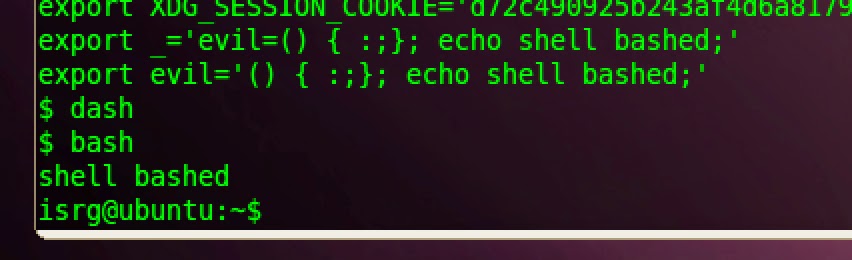
export command, in dash. We then load in the shellshock command at the command prompt within
dash, i.e., export evil= '() { :;}; echo shell bashed;' . Fig.2. shows the
command loaded up in export.
Fig. 2 – loading shell bashed
Fig. 3 – trying dash and then bash
We then run dash again to show that the command does not
run, and then bash to show that it does work.
Fig. 4 – Showing export in bash
From an investigative stance what is interesting is the fact
that while in bash, if we run export the evil variable is not shown even though
it is executed. Instead it is found in the env list, i.e., run env at command
prompt, and it is not the complete command, Fig.5.
Fig. 5 – env listing showing loaded evil variable in bash
Labels: bash, CVE-2014-6271, dash, env, export, investigation, main, shellshock, useful-commands




Post a Comment